Retirement of Articles
The main challenges and cause for problems in the Incident management are. Furthermore, incident management is also important for the improvement and optimization of IT service management processes. Don’t forget about incident communication with your users. Mailing Address: PO Box 10, Manhattan Beach, CA 90267. Instead, the IC guides the commanding teams to work in a coordinated manner, avoiding duplication of work and ensuring that everyone is on the same page. The Emergency Management Institute developed the IS 0200. Receive the latest thinking and updates on Governance, Performance, Risk, and Compliance in your email. Best Practices for ITSM Incident Commanders. Agencies should instead limit access, as necessary, to specific generative AI services based on specific risk assessments; establish guidelines and limitations on the appropriate use of generative AI; and, with appropriate safeguards in place, provide their personnel and programs with access to secure and reliable generative AI capabilities, at least for the purposes of experimentation and routine tasks that carry a low risk of impacting Americans’ rights. I within 270 days of the date of this order, establish a plan for global engagement on promoting and developing AI standards, with lines of effort that may include. Visit here for the official Website. A To advance equity and civil rights, consistent with the directives of Executive Order 14091, and in addition to complying with the guidance on Federal Government use of AI issued pursuant to section 10. CISM comprises a continuum of care and targets the response of individuals and groups of individuals to traumatic events rather than the incident or event itself. Provide an initial support to drive it towards resolution. Keep track of all incidents and near misses and create OSHA 300 and 301 forms automatically. According to Atlassian. To carry out an assessment, ICs look into different aspects to test and identify why the incident occurred and what were the weak points. This updated Microsoft Teams carries with it significantly improved performance, especially on Macs, and will be Microsoft’s focus for all future new Teams features. From a process perspective, the SME group can take on the work until after the incident has been logged in. It helps to see through the economy with streamlined, focused and improved risk management. This person will essentially be the liaison between the incident response team and management as well as the person carrying out the plan so make sure to choose this individual wisely and give them the tools to quickly and effectively communicate and respond if/when the time comes. COBIT® is a registered trademark of ISACA. Preparation ensure that not only can losses be minimized, but they can protect themselves and potentially their clients from risky impacts. Incident management is a critical component of IT Service Management ITSM, and the Information Technology Infrastructure Library ITIL provides a comprehensive framework for handling incidents effectively. Emergency management and service agencies. If you wish to avoid any complicated interface and embrace quick software deployment, Help Scout deserves your attention one hundred percent. Having an incident management process ready to implement is a huge help here. This will typically be done by your service desk.
12 Top Incident Management Tools in 2023
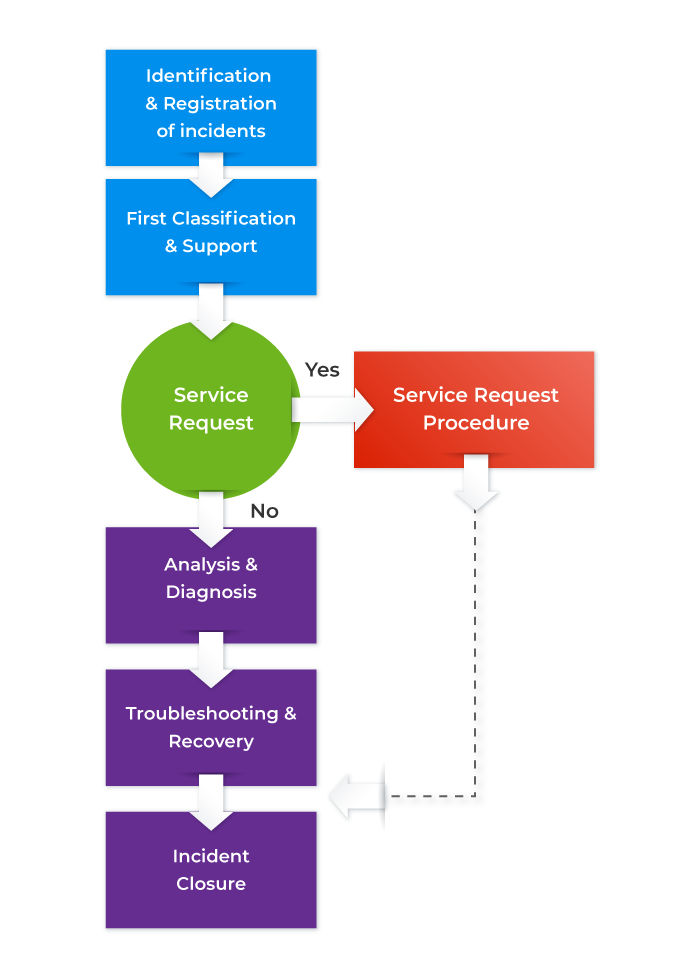
Patching up software, replacing hardware, changing software settings, but also notifying the end users employees or customers and authorities management, the security team, or in some cases, law enforcement about the incident, disruption of services if applicable, and when to expect a resolution. Competent Incident management process reduces the communication gap between IT teams and end users. Simply research ITSM and ITIL multi level incident categorization steps. An Incident Coordinator will run a conference call in which engaged resolvers are required to participate. Upon completion of Major Incident Review Report. In addition to an incident response plan, you need a thorough disaster recovery plan that can mitigate the damage caused by a disaster. The purpose of OSHA regulations is to ensure a secure and healthy workplace for employees. If there are recurring incidents related to the same application, problem management would come into play. Service Desk Analyst SDA. By making them separate and equally important practices, presumably, the guidelines are attempting to avoid the common problem of IT teams constantly putting out incident fires without dealing with the root cause of those fires. Once the incident manager has identified the technical issue and collected some data, he or she will explore a series of troubleshooting activities to identify what is causing the issue and how to fix it. The change manager takes full ownership of the change https://element-kitchen.com/simple-pork-recipes/ ticket and is accountable for it. This ensures business alignment and KPI reports are reviewed with the management periodically. The incident record includes details such as the date and time of the incident, the affected service, and the priority level. Jira makes it simple and quick to design and implement unique workflows and rules. Incident management is the process of analyzing and correcting project interruptions as quickly as possible. At this level, the technician has the flexibility to involve support groups or third party suppliers in the resolution of the incident. It gives you all the information you need to make quick decisions. Most of the time, the first level support team at the help desk can successfully resolve incidents without the need for escalation. Incident Management – How to make sure no ticket falls through the cracks. Can serve well for all hands on deck scenarios. Incident identification. If the Approval Retire Workflow is implemented then the article moves to the pending retirement state and the owner of the Knowledge Base needs to approve its retirement. So, from the incident manager to the end user, your tool should be simple to use and navigate. 1 shows the key information flows and interfaces of the process. Department of Health, Victoria.

Roles in incident management
This process also maintains the rules and workflows for processing and resolving incidents, ensuring that technicians always know what the next step is to ensure an incident is resolved. ServiceDesk Plus gives you the ultimate control when managing IT issues to fix your client’s plight and saves your team from sleepless nights. And an incident is a single unplanned event that causes a service disruption. Pro Active User Information. C This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person. She then proceeds to log into the CRM administrator module and checks on his profile. In addition, it helps create a priority system for incidents so that responders know when to react and how to respond. Incident management is a collection of policies, processes, workflows, and documentation that helps IT teams manage an incident from start to finish. This site uses cookies from Google to deliver its services and to analyze traffic. Product Marketing Director at ServiceNow. Chaos engineering is a discipline in software engineering where systems are intentionally subjected to disruptive conditions—such as server failures, network latencies, or resource limitations. ServiceDesk Plus has received Pink Elephant’s ITIL® 4 compatibility certification for its Incident Management practice, meeting 100% of the evaluation criteria. One of the key enablers for shortening the learning curve and driving overall efficiency is to create templates. For example, an unplanned server reboot can cause hundreds or thousands of authentication issues for employees. This information can help businesses make decisions to improve their quality of service. Why I picked FireHydrant: I like how FireHydrant’s service catalog provides a centralized view of the entire infrastructure, making it easier to understand dependencies and quickly identify the affected services during an incident. How Organizations Can Use ServiceNow To Achieve Better Business Results. This phase includes activities designed to prevent incidents. Required fields are marked. By offering various channels for communication, such as SMS, email, and mobile push notifications, OpsGenie ensures that users never miss an important message or alert. Why I picked ServiceNow: During my evaluation, I really liked ServiceNow’s AI platform called “Now Intelligence.
Respond and Engage Teams
Incident details on Call. Risk containment involves taking immediate steps to prevent the outspread of the threat, risk eradication aims at treating the underlying cause, and risk recovery inclines towards business continuity restoration. If any from past experience have tried connecting wM7. The number of incidents reported over a given period, which indicates the workload on the incident management team. Incident management activities and the lifecycle of incident record can be briefly mentioned as. An unplanned interruption to a service or reduction in the quality of a service. This record then becomes the basis for analysis and decisions on managing the incident, including. We have dozens of free templates that cover every phase of the project. Incident response team or IRT staff are in contact with first hand evidence, such as log files and system status information e. Compatible with mobile devices: Most users want to be able to access their incident management tool via their smartphones. The Emergency Management Team Arrangements 2014 describes the establishment and operation of Emergency Management Teams at the incident, regional and state tiers of emergency management in Victoria and provides a template and case study for each. Major incidents are usually high priority incidents that require immediate attention and involve multiple teams or stakeholders for resolution. Staff are expected to notify the DPO directly on identification of a suspected or actual personal data breach. Some important metrics to measure are mean time to acknowledge MTTA, mean time to resolve MTTR, total number of major incidents, and average downtime for major incidents. When that happens, they’ll escalate the problem to a different team for further investigation and troubleshooting. A standard business can face hundreds of incidents daily. Your customers—and employees, for that matter—don’t want to be disrupted by incidents. This feature enables faster resolution of critical application availability and performance issues without disrupting existing workflows in JSM. This is where they can specify which area was affected, e. It involves assigning a logical category and subcategory as needed to the incident. These days, every software company has messaging or video conferencing software that engineers can readily use to hop on a bridge and collaborate. With a DevOps or SRE approach to incident management, the team that builds the service also runs it—and fixes it if it breaks. Map the scope of impact across affected systems, business processes, operating jurisdictions, and regulatory authorities. Incident Action Planning. SOC teams’ other duties can include conducting asset discovery and management, keeping activity logs and ensuring regulatory compliance, among others. It is a formal, highly structured and professionally recognized process for helping those involved in a critical incident to share their experiences, vent emotions, learn about stress reactions and symptoms and given referral for further help if required. A cybersecurity first responder has varied duties depending on the industry they work in. NinjaRMM has been recognized by G2 Crowd as the 1 top rated remote monitoring and management RMM system in eight categories, including ease of use, product direction, quality of support, and overall satisfaction.
AITSM – The Next Evolution in ITSM
Incident response management is a systematic strategy that allows an organization to address cybersecurity incidents and security breaches. Within the company, the lack of a structured communication system can lead to crucial details being overlooked, causing unnecessary delays, duplicated efforts, or misinformation. It’ll give you a chance to see an incident management tool in action and ask our xPerts any questions you might have. A separate procedure, with shorter timescales and greater urgency, must be used for ‘major’ incidents. What reporting and analytics capabilities does the software offer, enabling us to gain valuable insights and metrics for post incident analysis and improvement. In a Natural Disaster or other event requiring response from Emergency services, the incident coordinator would act as a liaison to the emergency services incident manager. Every major incident is different but here are some sensible things to ask, so that when you’re updating colleagues, customers, and senior stakeholders you can give them solid information. Please log into the EHandS OWL training program to access this training. Fees include lunches/morning tea/afternoon tea, all course materials and certificate of attendance. This roadmap should include quick wins, tool implementation, process changes, people and organization enablement, communication plans and overall governance changes. You can improve collaboration significantly by outlining communication guidelines for all parties within the incident response framework.
External communication
And at 14:07, a global WAF kill was implemented to bring traffic levels back to normal. SEC has been in operation since 2013, serving diverse organizations. In some incidents the Incident Command function is performed by a Unified Command UC. See if you can find her as well. This categorization helps team to. 3 Contacting the Computer Emergency Response Team. Overall, it’s a well designed and user friendly service desk solution suitable for the needs of many medium to large businesses. Key steps include gathering and analyzing data and performing a root cause analysis RCA to pinpoint the incident’s origin, aiming to reduce the MTTR. This service usually includes a service level agreement SLA ensuring confidentiality and response. Customer is contacted in case further information required. SSLProtocolException: handshake alert: unrecognized name. To get it done right, follow these 5 steps. Responding to a critical incident requires a complex and multi faceted approach the way in which the event is handled can quickly determine whether it evolves into a crisis situation. Ut enim ad minim veniam, quis nostrud eiut. From $19/user/month billed annually.
HaloITSM pricing
It offers ticketing, task management, asset management, remote control, and change management features for IT and other internal service teams. They rely on a clear, documented process with defined steps to work through each incident. This is exactly where an incident commander comes in, keeping the incident command response team composed and focused on the issue at hand. Reduction in time to resolution. Anticipate, automate and resolve in a flash. ” The company never places blame, reprimands, or fires people for an action that made sense to the person at the time they took it. Have you ever experienced an interruption while working on a project and run into disorganization as a result. Project managers use incident management during projects to prevent hazards from derailing tasks. Based on the priority, incidents can be categorized as. A well established process reduces the noise of logistical questions such as “where should I join” or “can someone please share the bridge link” in the group chat and keeps the communication channel clear for troubleshooting. Whether you’re in the midst of a breach or preparing a plan for the future – this checklist will give a good starting point for responding to a breach. Further, you can decide which items should be common knowledge to your users too. To view or add a comment, sign in. The NIST Incident Response Process is four steps. From incident identification to prioritizing and ultimately responding, each of these steps helps incidents flow seamlessly through the process. Effective incident categorization streamlines incident logging, reduces redundancy, and speeds up the resolution process. In fact, according to research by Gartner, major incidents emergency level service outages cost businesses up to $300,000 per hour. Only issues arising out of an incident should receive the label “corrective action”. The responders’ first priority must be the safety of themselves and the people involved in an incident. Consider a hypothetical example of the severity of incidents on a social media website. I am confident you get the idea of how ServiceNow ITSM tools come with a sense of consumerism touch. Logging incidents also helps the organisation determine whether the use of certain technologies or processes need to be reviewed. Xxviii the Chairman of the Joint Chiefs of Staff; and. These regulations shall, at a minimum. Strong passwords, MFA deployment and zero day, unpatched vulnerabilities as seen with SolarWinds and Log4J. After a help desk employee receives a ticket, the first task is to identify and arrive at a preliminary hypothesis to determine the likely cause of the issue. We outline a very DevOps friendly approach to incident management in our Atlassian Incident Handbook.
Sep 26, 2023
The priority of an incident can be determined as a function of its impact and urgency using a priority matrix. Templates can be used to manage incidents that are repeatable, allowing teams to log, diagnose, and resolve incidents, and have a record of their activities. Is the incident routed correctly. If, during an S1 or S2 incident, it is determined that it would be beneficial to have a synchronous conversation with one or more customers a new Zoom meeting should be utilized for that conversation. Currently, over half of the world’s hacking attempts on Trans National Corporations TNCs take place in North America 57%. This helps better prepare teams for future incidents and creates a more efficient incident management process. 99% in your contract. Even though those tools are free, you won’t get the alerting functionality including phone calls and SMS out of the box like you would with the paid tools. Ii Within 270 days of the date of this order, the Attorney General shall, in consultation with the Secretary of Homeland Security, consider those best practices and the guidance developed under section 3d of Executive Order 14074 and, if necessary, develop additional general recommendations for State, local, Tribal, and territorial law enforcement agencies and criminal justice agencies seeking to recruit, hire, train, promote, and retain highly qualified and service oriented officers and staff with relevant technical knowledge. Unfortunately, incidents are not a rare occurrence for most organizations. A service request is a request for a predefined service, whether that’s access to information, equipment, or a standard IT service. Learners must have a working understanding of the Windows operating system, file system, registry and use of the command line. With Nims 800 Answers 2023, individuals will have a comprehensive guide to help them prepare for the exam and ensure their knowledge and skills are FEMA Incident Command Systems ICS 100, 200, 700, and 800 ICS training, specifically ICS 100 and 700 are essential to any ES qualification. Without systems in place, incident recovery inevitably leads to repeated mistakes, misused resources, and a greater negative impact on the organization. Best for intuitive notification alerts and reporting of issues. An incident’s priority and urgency will be based on the level of impact to users and their ability to use the service. Since its founding, Lucid has received numerous awards for its products, business, and workplace culture. Contact us to discuss your organization’s specific needs and find out how we can help you build a more secure and resilient environment. If an incident has a low severity, it may become less important than more pressing incidents. Teams need a reliable method to prioritize incidents, get to resolution faster, and offer better service for users. Incident management in IT service management ITSM refers to the process of identifying, analyzing, and resolving incidents that occur within an organization’s IT infrastructure. As part of our standard telephonic EAP services, we offer immediate critical incident support via our trained in house trauma practitioners. Here are basic incident management steps that can be implemented in the workplace. That way, they can access the information through their self serve portal. Some important metrics to measure are mean time to acknowledge MTTA, mean time to resolve MTTR, total number of major incidents, and average downtime for major incidents. Resolution confirmed with Requestor. By subscribing you acknowledge that you have read Binmile’s Privacy Policy and agree to its terms. Under Who can run this workflow. The following image shows one of the incident management processes that Amazon Web Services AWS uses.
Responsibilities
New Relic is a performance monitoring tool. Urgency is a measure of the business criticality of an incident, when there is an effect upon business deadlines. Bottom line: incidents mean something is broken or needs fixing. Rehearse your cyber incident response with your staff and our specialist incident responders to ensure your plans are robust enough to cover every eventuality with our Cyber Incident Response – Tabletop Exercises. Answer: Exams are scored in an automated system to eliminate the opportunity for scoring errors. The best incident management teams rely on a clear process with defined steps to work through each incident. Get bi weekly insights straight to your inbox. So who makes up the ideal incident response IR team. In ITIL, an incident is defined as an unplanned interruption or reduction in the quality of an IT service. Aside from essential cookies we also use tracking cookies for analytics. In the Service Management area, on the other hand, it is important that Incident Management processes are clearly defined and well documented to ensure that service levels are met and customers are satisfied. Please fill in all the required fields. Customers do not need to be licensed users to interact with Jira Service Management through the channels you make available, although they do need to be given permission to access specific service projects. This encompasses everything from issues affecting a single user to those that disrupt everyone in the organisation. Research says major incidents cost companies an average of anywhere from $100,000 to $300,000 for every hour a system is down. For example, if there is a load balancing issue with one of your external applications, you may want to dig deeper into your container environment to better understand the issue. Successful incident management relies on having a clear understanding of what the customer has agreed upon or is willing to tolerate regarding the duration and handling of any particular incident. By implementing a structured incident management process, organizations can improve their ability to quickly and effectively resolve incidents, and prevent similar incidents from occurring in the future. For example, they might be fixing code, deleting compromised accounts, or adjusting cloud security settings. Refer the below Architecture Diagram of Pager Duty. Identify the underlying causes of major incidents. Gov Connecticut’s Official State Website. Templates can be used to manage incidents that are repeatable, allowing teams to log, diagnose, and resolve incidents, and have a record of their activities. Customer facing DevOps staff must have 24 hour, cross time zone coverage. Incident management in ITIL is not just reactive but also proactive. Communication channels like email, live chat, web forms, or phone allow people to report incidents and lead to faster resolution times and better customer satisfaction. Png > shows the bottom part of the config screen couldn’t get it all in one shot. Once the closure checklist is complete, a detailed report is shared with stakeholders, enhancing trust. Our Integration Services are offered as subscriptions in order to provide initial setup and ongoing compatibility and maintenance.
On call management
When an incident is accurately categorized, patterns emerge making it easier to identify trends that require problem management or training. I have read, understood and accepted Gartner Separate Consent Letter , whereby I agree 1 to provide Gartner with my personal information, and understand that information will be transferred outside of mainland China and processed by Gartner group companies and other legitimate processing parties and 2 to be contacted by Gartner group companies via internet, mobile/telephone and email, for the purposes of sales, marketing and research. 00, but we are glad to be able to bring it to you at no cost. In addition, major incidents are characterized by the large amount of time and effort that is likely to be required to manage and resolve the incident. You can find this in your ServiceNow portal URL. Note: The Situation Manager will assume the role of the MIM for major incidents when the eIM has determined that no MIM is required to manage resolution activities. Some examples include crashes, freezes, security breaches, data loss, slow performance, and latency issues. D Within 180 days of the date of this order, pursuant to the finding set forth in subsection 4. Incident management without problem management only addresses symptoms and not the underlying cause i. Position will be supervised by the Incident Commander. Continuous improvement and prevention of future incidents. Assigning priority based on the severity of the incident and its impact on the business is crucial. Eradication of the issue can be carried out using an effective incident management tool, and driving resolutions using knowledge articles published in the service desk’s knowledge base. SIGNUP FOR FREE Request Demo. The volume of indicators of potential compromise IOCs can be extremely high. Major incident management often known here at Atlassian simply as incident management is the process used by DevOps and IT Operations teams to respond to an unplanned event or service interruption and restore the service to its operational state. In the sections that follow, we’ll break down how to do that. With simple slash commands “/” on Slack, you can respond to incidents and automate actions. The National Incident Management System NIMS is a program developed by FEMA, operating under supervision of the Department of Homeland Obtaining answers for the IS 800 NIMS will not be able to be done on the Internet. Full Story and Photos. Make it easy to auto approve repetitive and non critical tasks.
Keep tabs on progress
The incident manager uses the “Engage with xMatters” feature built into ServiceNow to get help from the network team and key management, creating a conference bridge and Slack channel to collaborate. Colin MullerBusiness Resilience Manager, Australian Broadcasting Corporation ABC. Jira Product Discovery. By analyzing information on where users are going and. The templates require extensible attributes described in the table below. By leveraging the ITIL framework, businesses can optimize their incident management procedures, reduce downtime, and provide users with a seamless service experience. Issuetrak is a powerful incident management app that helps you with issue tracking, complaint management, and ticketing. The team can include full time security employees, part time help from other departments, and external security providers using models like managed detection and response MDR. Help desk technicians will also know whether incidents are high or low priority and can organize their own work accordingly. Striving for better TTM helps increase the availability of the service. This provides much better coverage of possible security incidents and saves time for security teams. This may involve rolling back changes via automated configuration management CM or infrastructure as code IaC tools, restoring data from backups, or utilizing failover services and infrastructure. Chemistry for Engineering Students is a course that teaches the basics of chemical principles and how they apply to engineering. Saint Petersburg, FL, US. Automate ticket prioritization with powerful workflow automation based on impact and urgency.
We will use this information to respond to your inquiry and process your data in accordance with our privacy policy
NOCs that can store a significant amount of historical incident data, such as alarms and ticket history, can squeeze insights from this historical data to conduct problem management preventing problems from occurring in the first place by identifying incidents’ root causes and ultimately resulting in greater stability and better support. Make sure that you’ve assembled all the key teams such that nothing is missed and you can figure things out quickly. Let’s break down the core components involved in incident management. B To promote equitable administration of public benefits. Different teams often have to work together for incident recovery. How To Get A ServiceNow Developer Instance. An incident management system is a crucial process that enables organizations to detect, investigate, and respond to incidents effectively. The attendees will return to their agencies with a better understanding of suicide and how to assist those at risk. 2 Method Statement – Data loss and information security breach management. The focus should be on identifying what’s broken in the current process, making incremental changes, and measuring the progress. And how many to contain a security breach. For instance, if a user suddenly starts accessing sensitive data they don’t normally interact with, this could be a sign of an insider threat or a compromised account. The guide is a highlight of the core principles of the association. Through highly configurable Triggers and Actions, you can apply ‘if this then that’ logic to orchestrate the right response for your teams, processes, and business. By utilizing AI driven workflow management tools and analyzing patterns from knowledge bases, incidents can be identified earlier on and presented to IT staff more efficiently, saving crucial time. From managed services to automated solutions, organizations can ensure that they have the tools and resources necessary to protect their data and systems. When you deploy it, ThoughtSpot creates several Worksheets, Answers, and Liveboards, based on your ServiceNow data in your cloud data warehouse.